How to prevent Linux OOM from killing Charon processes
Table of contents
Description
When a Linux system runs very low on memory, the kernel will begin killing processes to free ram. The mechanism responsible for this is called the OOM Killer. Because Charon processes can consume quite a lot of memory, it is a good candidate that can be killed. Therefore, it is important that Charon processes be protected from this..
Related Operating Systems: Red Hat Enterprise Linux 6, 7 & 8, CentOS 7 & 8
Identification of the problem
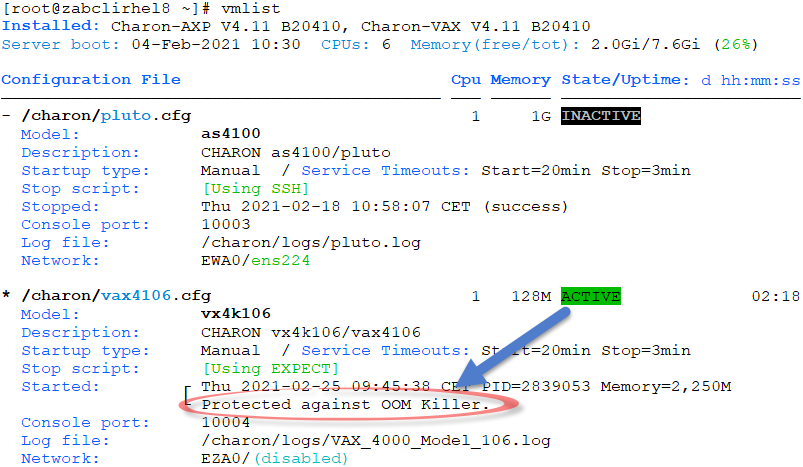
The Charon process is killed and no information is reported in the log file.
The information can be found in the /var/log/messages file or, depending on your Linux distribution, using the journalctl command
Example - /var/log/messages report:
...
|
Example - journalctl command:
...
|
Step-by-step guide
Manual steps
By process
OOM killer exclusion is done on a process by process basis by changing the corresponding kernel parameter associated with a particular process. Example::
|
Therefore, it is necessary to know all the PID of all the Charon processes and then feed them into the command. Using the Linux command “pgrep” we can list all the Charon processes and then prevent them from being killed:
|
This action can be automated by running a cron job regularly to update the oom_adj entry. This is a simple way to ensure that Charon processes are excluded from OOM killer. An example cron job entry is listed below:
|
The job will run at every 30 minute and update the oom_score_adj of the current running Charon processes.
By service
Edit the service (systemd) configuration file you created to start your Charon emulator and add "OOMScoreAdjust=-1000" under the "[Service]" part.
After editing the file, a reload of the services definition is necessary using the command: # systemctl daemon-reload
Example:
Here we want to protect aksusbd service (HASP license service) from being killed:
# systemctl cat aksusbd
|
# vim /etc/systemd/system/aksusbd.service
... |
# systemctl daemon-reload
# systemctl restart aksusbd
![]() the same operation can be performed for
the same operation can be performed for hasplmd service
![]() In case of upgrade or reinstallation, OOMScoreAdjust line could be removed.
In case of upgrade or reinstallation, OOMScoreAdjust line could be removed.
Linux Toolkit
Starting with the Linux Toolkit version 1.47, the Charon virtual machines processes can be protected against OOM Killer directly from the menu, "Preferences" option.
![]() The Linux Toolkit is available for Charon-AXP, Charon-VAX and Charon-PAR only.
The Linux Toolkit is available for Charon-AXP, Charon-VAX and Charon-PAR only.
Example:
Links
redhat Solutions - How to disable the Out of memory or oom-killer?
redhat Solutions - How to prevent a process to be a target of oom-killer?
Related articles
© Stromasys, 1999-2024 - All the information is provided on the best effort basis, and might be changed anytime without notice. Information provided does not mean Stromasys commitment to any features described.