Table of contents
‘vi’ and 'vim' text editors
Notes:
- When typing text, press <ESC> once finished. In case you’re blocked, press also <ESC> before executing commands described below
- both editors use case sensitive commands
Request | Command |
To quit without saving | Press ‘:’ then enter ‘q!’ |
To quit with saving | Press ‘:’ then enter ‘x’ or ‘wq’ |
Go to top of file | Press ‘:’ then enter ‘0’ |
Go to last line | Press ‘G’ |
Search pattern | Press ‘/’ then enter your search text. Press then ‘n’ for next (forward) or ‘N’ for backward |
Remove current character | Press ‘x’ |
Insert text | Press ‘i’ (press ESC once text completed) |
Insert line | Press ‘o’ for a line below cursor, ‘O’ for a line above cursor (press ESC once text completed) |
Delete a line | Press ‘dd’ |
‘gedit’ graphical editor
‘gedit’ is a graphical text editor, users familiar with Windows notepad should not encounter difficulties to use it.
Request | Command |
To quit | close the window by clicking on the cross top right corner |
Save file | Press <CTRL-S> |
‘nano’ text editor
‘nano’ is a basic text editor, very simple to use and displaying available commands at the bottom of the screen. For example, to leave ‘nano’ , use ^X (press CTRL + X)
How to setup ‘ssh’ trusts between Linux and Tru64
Notes
- The prompts will tell you where to execute the commands, "
Tru64#" (root user) or "Linux#" (root user) - Remember Linux/Unix is case sensitive
- If hosts are not known by each other, fill the
/etc/hostsfile for example (usingvifor example) - linuxhost represents the name of your CHARON server (can be any name you want)
- tru64host represents the hostname of your Tru64 virtual machine
- Generate the key
→ Do not specify a passphrase |
- Copy the linuxhost.pub file, or use copy/paste, in the /.ssh2 folder on the Tru64 host
- Define the authorization file:
|
- Initialize the first ssh connection (answer '
yes' to confirm)
|
then retry the same command to verify the trust is working.
![]() If an error occurs, you can check and clean the
If an error occurs, you can check and clean the /root/.ssh/known_host file on the Linux host
How to setup ‘ssh’ trusts between Linux and VMS
Notes
- The prompts will tell you where to execute the commands, "
VMS$" (system user) or "Linux#" (root user) - Remember Linux/Unix is case sensitive, VMS is not
- Linux: if VMS host is not known, add it to
/etc/hostsfor example - VMS: if Linux is not known, add it using:
$ UCX SET HOST LINUX /ADDR=xx.xx.xx.xx
Enable SSH on the VMS server:
VMS$ SET DEF SYS$LOGIN
VMS$ @TCPIP$CONFIG
- Select then:
Option 3 - Server components then enable and start service SSH, option 19then
Option 2 - Enable & Start service on this node...
* Create a new default server host key? YES: YESCreating private key file: TCPIP$SSH_DEVICE:TCPIP$SSH.SSH2]HOSTKEY
...
Generate the key on the Linux server and convert it to be readable by VMS
Linux# ssh-keygen -t rsa→ Do not specify a passphrase
Linux# ssh-keygen -e -f /root/.ssh/id_rsa.pub > /root/.ssh/linuxserver.pub
- Copy the generated file
/root/.ssh/linuxserver.pub(or use copy/paste between putty session for example) to the VMS system in theSYS$SYSROOT:[SYSMGR.SSH2] directory If this folder does not exist, create it using the following command:
If this folder does not exist, create it using the following command: $ CREATE /DIRECTORY SYS$SYSROOT:[SYSMGR.SSH2]
On the VMS system add the Linux server key to the authorized keys:
VMS$ SET DEF SYS$SYSLOGIN
VMS$ SET DEF SYS$SYSROOT:[.SSH2]
VMS$ OPEN/WRITE TMP AUTHORIZATION. If the file already exists, use
If the file already exists, use /APPENDinstead of/WRITE
VMS$ WRITE TMP "KEY LINUXSERVER.PUB"
VMS$ CLOSE TMP Do not forget the dot at the end of the authorization file name
Do not forget the dot at the end of the authorization file name
Perform some tests (examples)
 Charon server name "charon", vms system name "pluto":
Charon server name "charon", vms system name "pluto":charon# ssh system@pluto "show system /noproc"
OpenVMS V7.3-2 on node PLUTO 27-SEP-2013 11:50:14.37 Uptime 0 19:20:07
How to setup ‘rsh’ trusts between Linux and Tru64
Introduction
RSH executes commands on a remote host. It can be used to issue a shutdown on the Charon Tru64 virtual machine.
Pre-requisites
The RSH method requires the 'rsh' package. It can be installed using the following command:
# yum install rsh |
Notes
On the Tru64 system issuing the shutdown, create a proxy between the root user of the Charon server and the user.
Example ('ceres' is the Charon server name):
# echo "ceres root" >>~/.rhosts |
If the Charon server name is not known to the TCPIP database, edit the /etc/hosts file and add the server ip address and its name.
Ensure manual commands can be passed to the Tru64 system from the Charon server.
Example ('pluto' is the Tru64 hostname):
# rsh pluto date |
If a "poll: protocol failure in circuit setup" is returned, the firewall settings have to be set to open ports 113 and 1022.
Please always refer to your network administrator when changing the firewall rules, commands below are given as example only.
Example for Red Hat Enterprise Linux 6.x servers:
|
Example for Red Hat Enterprise Linux 7.x and CentOS 7.x servers:
|
How to setup ‘rsh’ trusts between Linux and OpenVMS
Introduction
RSH executes commands on a remote host. It can be used to issue a shutdown on the Charon OpenVMS virtual machine.
Pre-requisites
The RSH method requires the 'rsh' package. It can be installed using the following command:
# yum install rsh |
Notes
RSH and REXEC services must be available on the OpenVMS virtual machine. This depends on the OpenVMS version and a valid UCX license is required.
To enable these services, run @SYS$MANAGER:TCPIP$CONFIG, select the "Client components" and then enable and start "REXEC and RSH" services.
Create a proxy between the root user of the Charon server and the user on the OpenVMS system issuing the shutdown.
Example ('ceres' is the Charon server name):
$ tcpip add proxy system /remote="root" /host=ceres |
If the Charon server name is not known to the TCPIP database, use the following command to add it.
Example:
$ tcpip set host ceres /address=1.2.3.4 |
Copy charon_shutdown.com script located in the /opt/charon/utils folder to SYS$MANAGER:CHARON_SHUTDOWN.COM on the OpenVMS system (using copy/paste for example). This is required as if the shutdown is executed directly from the 'rsh' command directly, 'rsh' will not timeout when the shutdown will be completed and the virtual machine will not be stopped cleanly, it will timeout depending on the service settings.
Ensure manual commands can be passed to the OpenVMS system from the Charon server.
Example ('vms084' is the OpenVMS hostname):
# rsh -l system vms084 "show time" |
If a "poll: protocol failure in circuit setup" is returned, the firewall settings have to be set to open ports 113 and 1022.
Please always refer to your network administrator when changing the firewall rules, commands below are given as example only.
Example for Red Hat Enterprise Linux 6.x servers:
|
Example for Red Hat Enterprise Linux 7.x and CentOS 7.x servers:
# firewall-cmd --permanent --new-service=Charon# firewall-cmd --permanent --service=Charon --add-port=113/tcp# firewall-cmd --permanent --service=Charon --add-port=1022/tcp# firewall-cmd --get-active-zonespublic interfaces: ens34 ens35# firewall-cmd --zone=public --permanent --add-service=Charon# firewall-cmd --reload |
Shutdown guests with Expect tool
Introduction
In case SSH cannot be used to perform clean shutdown of the guests, the "expect" tool can be used to connect to the console, perform the login operation and execute the shutdown command depending on the console status (at login prompt, shell prompt or SRM prompt)
![]() In this case the password is sent without encryption.
In this case the password is sent without encryption.
To facilitate use of "expect" for shutdown, an example is provided in the "guest_shutdown.exp" script located in the /opt/charon/utils folder. If you plan to customize the script, you'll have to create a copy and not use it directly as it will be overwritten in case of Toolkit upgrade.
'telnet' and 'expect' packages must be installed in order to use this feature.
The following error message can be returned when stopping the virtual machine when trying to use the expect script example:
- if expect package is not installed: "
Stop script returned error code 126". - if telnet is not installed: "
%EXPECT-F-NOSRM, Cannot continue, 'telnet' is not installed" then "Stop script returned error code 4"
Caution: the virtual machine process will be however killed by service management process
Console locked:
Any active session to the console must be killed before the "expect" script is executed.
![]() For example, if you are connected via "
For example, if you are connected via "telnet" on the localhost/port (the kill is not done inside the expect script). Using the "/opt/charon/utils/charon_gstart_expect" script file the necessary operations will be performed.
![]() If the console is locked from another host (if you use
If the console is locked from another host (if you use putty for example), you will have to cancel the connection by yourself otherwise the shutdown will not be performed cleanly.
This script can handle the following situations:
- No user connected on the console:
- Expect: "
Username:" (VMS) or "login:" (Tru64) - Action: An interactive session will be initiated based on <user> and <password> provided in the parameters
- Expect: "
- A user is connected on the console:
- Expect: <prompt> provided in the parameters
 This user must have privileges to perform shutdown as no logout will be issued
This user must have privileges to perform shutdown as no logout will be issued- Action: Depending on the Operating system parameter (see <opsys> below), the shutdown command will be sent
- Console is at SRM prompt:
- Expect: ‘
>>>’ (so works with VAX and Alpha with "P00>>>") - Action: A '
power off' command will be issued. If the command is not recognized, the F6 key will be sent (this must be enabled within the configuration file). If the F6 key did not stop the emulator, the script will exit with error code 9 meaning you will have to kill the emulator process yourself. Using the "/opt/charon/utils/charon_gstart_expect" script file the necessary operations will be performed.
- Expect: ‘
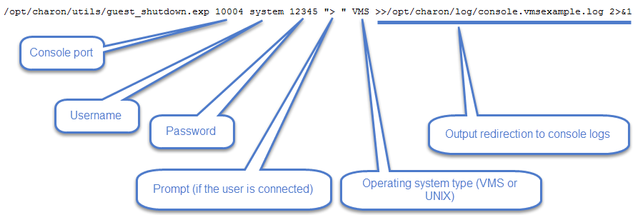
Script usage
Usage:
# path/script <port> <user> <password> <prompt> <opsys>
Parameters:
| Parameter | Description |
|---|---|
| <port> | telnet port number (example: 10003) |
| <user> | username for login (must be able to perform shutdown) |
| <password> | password |
| <prompt> | shell prompt (including end space) or last characters of the prompt |
| <opsys> | VMS or UNIX |
Example:
How to restart CHARON-VAX/AXP on Linux automatically on failure
![]() This part only applies to Linux distributions using
This part only applies to Linux distributions using systemd thus Red Hat Enterprise Linux 6.x versions are not concerned.
- Edit the service configuration file and add the following parameters using the "VM Management" option from the menu then "Manage 'systemd services".
- Update the service and server boot parameters as described in the appendix How to restart Charon-VAX/AXP on Linux automatically on failure